A distribution campaign for a new ransomware called Nozelesn is currently underway that is targeting Poland. This campaign started July 1st and we already have reports from victims in our forums and numerous cases have been spotted on ID Ransomware.
MalwareHunterTeam noticed numerous submissions to ID Ransomware from Poland and a new topic created by victims in the BleepingComputer forums.
A researcher at CERT Polska, the Computer Emergency Response Team for Poland, has also stated that they believe the ransomware is being distributed through a spam campaign pretending to be a DHL invoice.
Unfortunately, the campaign’s appear to be dead and we have not been able to find sample of the actual ransomware.
What happens when you are infected with the Nozelesn Ransomware
As a sample of Nozelesn Ransomware has not been found as of yet, the only information we currently have is based on the reports by victims who have posted to Twitter and in our forums.
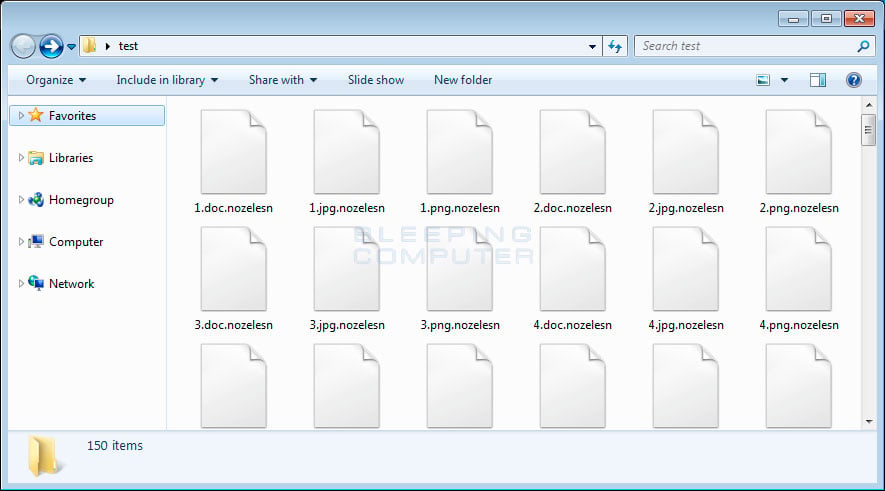
What we know is that the ransomware will encrypt a user’s files and append the .nozelesn extension to the encrypted file’s name. You can see an example of what an encrypted folder would look like below.
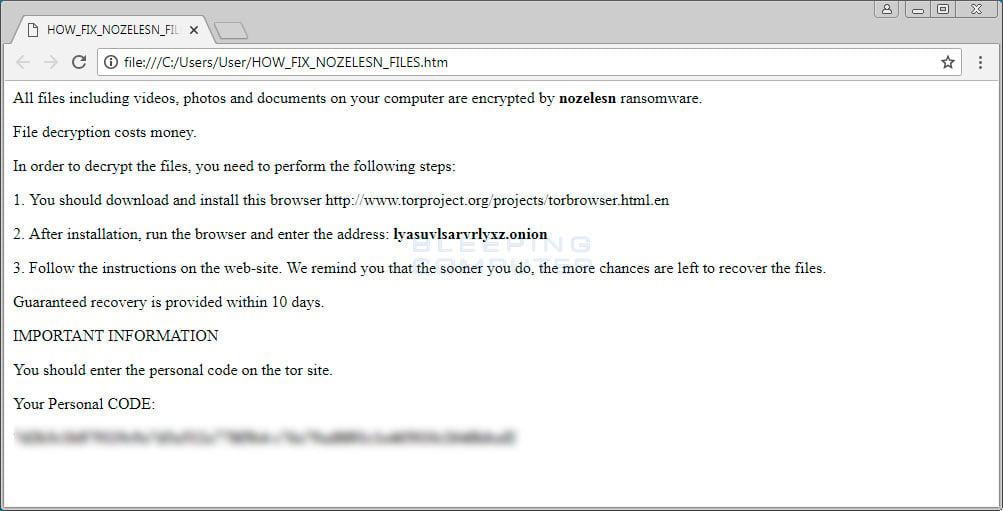
The ransomware will also create ransom notes on the computer named HOW_FIX_NOZELESN_FILES.htm. This ransom note contains isntructions on how to login to a TOR payment server at lyasuvlsarvrlyxz.onion to receive instructions. It also contains a unique personal code that the victim will be need in order to login to the server.
The TOR payment server is described in the next sections:
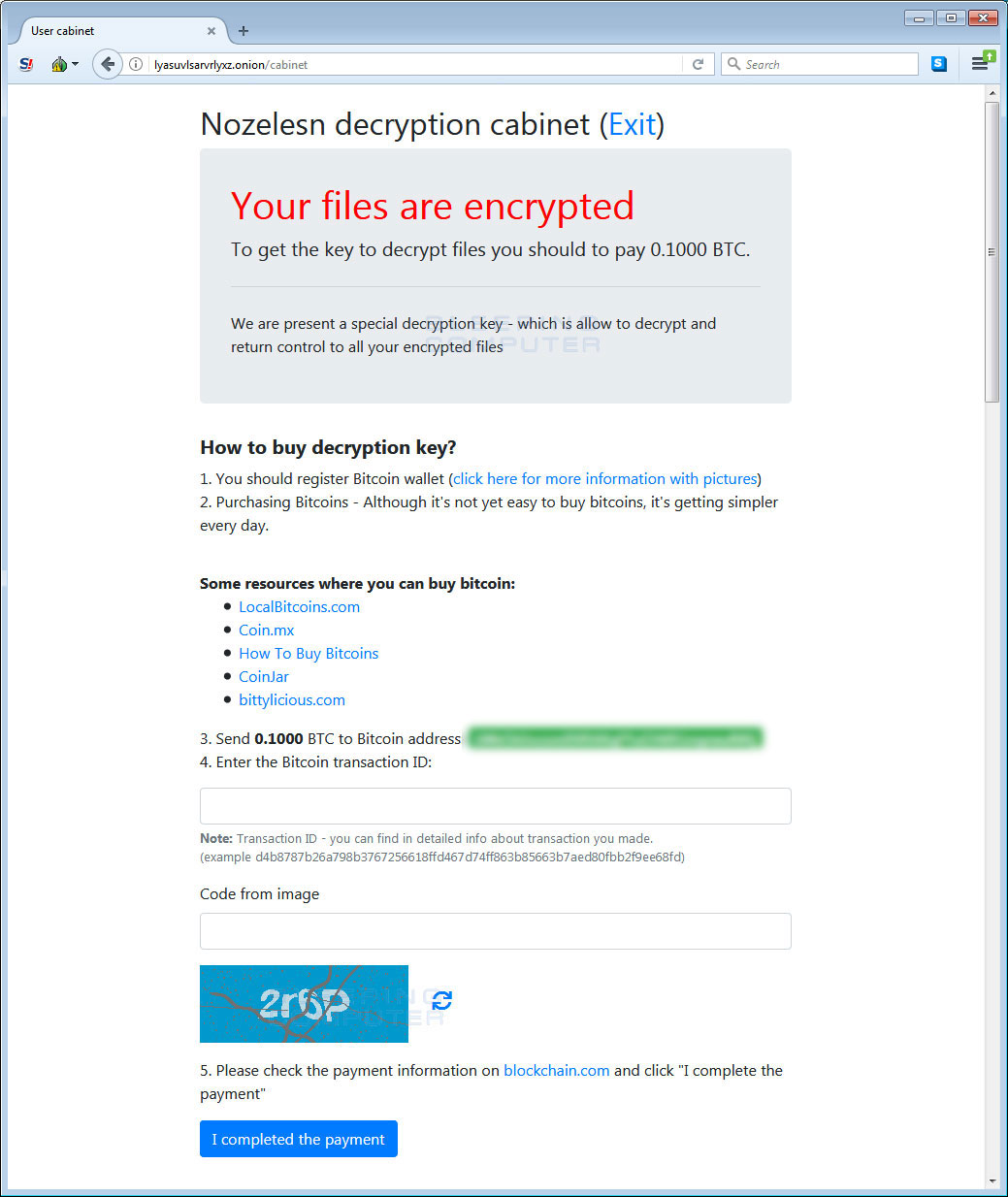
The Nozelesn decryption cabinet
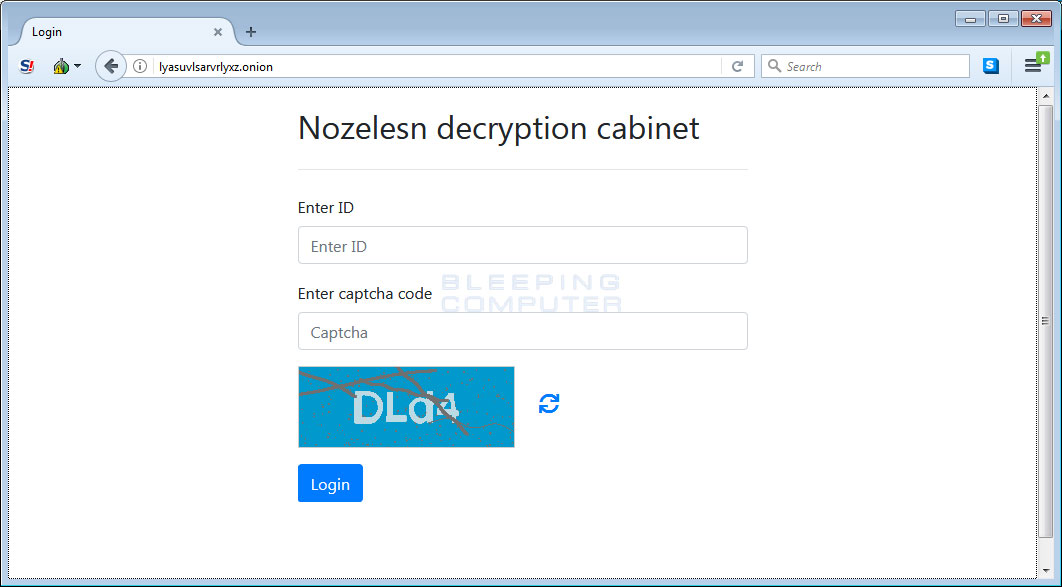
The TOR Payment server for this ransomware is called the “Nozelesn decryption cabinet” and is located at the lyasuvlsarvrlyxz.onion address. When you first visit the site you will be required to enter the personal code from your ransom note and a captcha answer into the login screen.
Once logged in you will see payment instructions that contain the amount of bitcoins to send and the address to send them to in order pay the ransom. Currently the ransom payment amount is set to .10 bitcoins or approximately $660 USD.
It is not known if paying the ransom will result in getting a decryption key and it is strongly advised that you do not pay the ransom. Instead try and restore from backups or Shadow Volume Copies if they are available.
Once a sample is found, it will be analyzed to determine if a victim’s files can be decrypted for free.
How to protect yourself from the Nozelesn Ransomware
In order to protect yourself from ransomware in general, it is important that you use good computing habits and security software. The most important step is to always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also make sure that you do not have any computers running remote desktop services connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
A good security software solution that incorporates behavioral detections to combat ransomware and not just use signature detections or heuristics is important as well. For example, Sophos Endpoint advanced and Sophos InterceptX both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
Last, but not least, make sure you practice the following security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Do not connect Remote Desktop Services directly to the Internet. Instead, make sure they can only be accessed by logging into a VPN first.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed that uses behavioral detections or white list technology. White listing can be a pain to train, but if your willing to stock with it, could have the biggest payoffs.
- Use hard passwords and never reuse the same password at multiple sites.
- BACKUP!
IOCs
File names:
HOW_FIX_NOZELESN_FILES.htmRansom note text:
All files including videos, photos and documents on your computer are encrypted by nozelesn ransomware.
File decryption costs money.
In order to decrypt the files, you need to perform the following steps:
1. You should download and install this browser http://www.torproject.org/projects/torbrowser.html.en
2. After installation, run the browser and enter the address: lyasuvlsarvrlyxz.onion
3. Follow the instructions on the web-site. We remind you that the sooner you do, the more chances are left to recover the files.
Guaranteed recovery is provided within 10 days.
IMPORTANT INFORMATION
You should enter the personal code on the tor site.
Your Personal CODE:
[id]Associated network addresses:
lyasuvlsarvrlyxz.onion
Source
https://www.bleepingcomputer.com/news/security/nozelesn-ransomware-reportedly-using-spam-to-target-poland/

